Summer is supposed to be a quiet season. It’s the time when employees go on vacation. Work slows down. Most emails get answered with automatic holiday replies. But while businesses relax, cybercriminals get to work.
Recent research shows that holiday periods create a perfect storm for attackers. The number of cyber incidents spikes by almost half, and June alone has seen jumps of up to 60%. With fewer people watching security dashboards and teams working with minimal staff, small mistakes are easy to miss. Those little oversights can quickly turn into open doors for data theft and system breaches.
This season, one particular scheme has stood out. A fake coding assignment was sent to developers
Scammers impersonate recruiters or potential clients. They send what appears to be a harmless test task. In reality, the risks are serious and affect two main groups:
- For freelancers, the damage isn’t limited to wasted hours of unpaid work. These assignments can also hide malicious scripts designed to steal data or infect the device.
- For in-house developers, the risk is even higher. Opening or running that infected test code on a company computer can put internal systems at risk and give attackers a way into the network. Once inside, they can expose sensitive client information and even cause a full-scale corporate breach.
How fake test assignments reach developers
From a security perspective, these scams follow a classic pattern. Attackers introduce malicious payloads under the guise of legitimate workflow artifacts. In this case, the artifact is a “test assignment”. Developers are conditioned to accept it without hesitation. By exploiting professional trust, adversaries bypass the usual suspicion applied to unknown links or executables.
Freelancers as primary targets
Threat actors frequently impersonate recruiters or clients on professional platforms like LinkedIn, Upwork, Fiverr, or GitHub. The pretext is the submission of a trial task prior to engagement. Delivery vectors include archive files, links to external repositories, or seemingly benign code snippets. Because unpaid trial work is normalized in the freelance ecosystem, malicious files are often opened without scrutiny.
In-house developers as secondary entry points
Within organizations, attackers use spear-phishing emails, social engineering on LinkedIn, or GitHub collaboration invites. The objective is to deliver code directly onto corporate endpoints. Once the code runs, it can significantly widen the attack surface. From there, attackers can move through internal systems and steal login credentials.
The common denominator in both cases is abuse of professional trust channels. Unlike generic phishing, these attacks blend seamlessly into established development practices, making them harder to detect and easier to rationalize as usual.
What happens when malicious test code runs
On the surface, a fake coding assignment looks like any other test task. But behind the scenes, it can trigger a whole infection chain. The FogDoor campaign executed in 2023 is a real example of how it works.
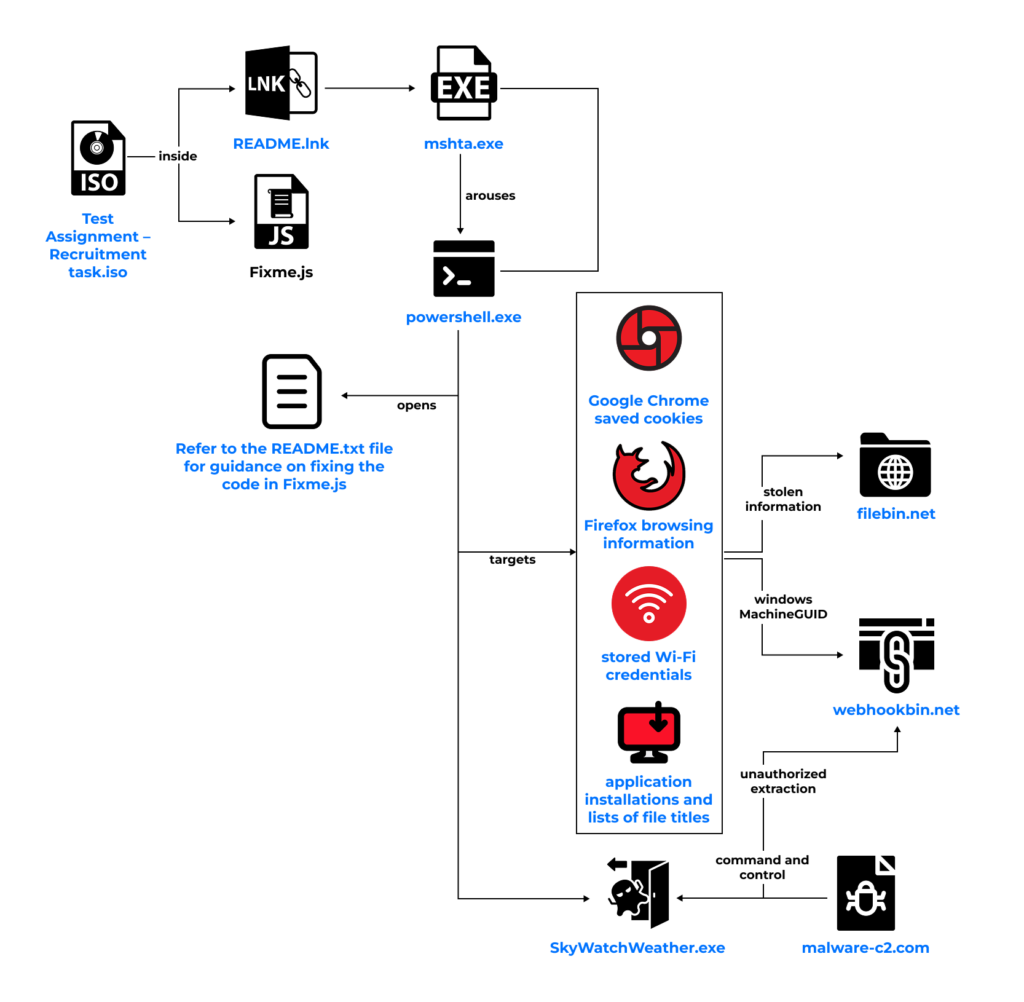
1. A fake assignment arrives as an ISO file
Developers receive an ISO file (a type of compressed folder) named something like “Test Assignment – Recruitment task.iso.” Inside are a few files. A short README with instructions and a simple coding exercise, such as FizzBuzz.js. Nothing seems suspicious at first glance.
2. The README secretly launches malware
Alongside the assignment is a disguised shortcut file (README.lnk). Clicking it secretly launches a built-in Windows tool (mshta.exe) that pulls down a malicious script from the Internet. So, while the developer thinks they’re opening instructions, the computer is already fetching malware.
3. Your system data is stolen
The downloaded script runs through PowerShell (a Windows automation tool). And begins harvesting sensitive information, such as:
- Browser cookies (which can contain login sessions)
- Saved Wi-Fi passwords
- Lists of installed apps and files
- Unique system identifiers that make the machine traceable
4. The stolen data is sent to the attacker’s servers
Everything is quietly uploaded to attacker-controlled servers. At this point, your accounts, passwords, and system fingerprints are in someone else’s hands.
5. A backdoor is installed for future access
The malware drops a persistent program (SkyWatchWeather.exe) that acts as a backdoor. This ensures attackers can come back later, issue new commands, and even spread through a company’s internal network.
How to spot and protect against fake coding assignments
Scammers have learned that developers are naturally curious and eager to prove their skills. This makes test assignments a perfect trap. But careful checks can help you avoid falling into their traps. Here are the most important red flags and protective steps, tailored for both freelancers and in-house developers:
Red flags to watch out for
- Assignments sent from personal email accounts (Gmail, Yahoo, Outlook) instead of official company domains.
- Unverified recruiters who can’t provide a LinkedIn profile, an official job posting, or company details.
- Test tasks that require downloading unusual file formats like .iso, .exe, or .scr rather than a text file or GitHub repo.
- Code that looks obfuscated or overly complex for what should be a simple test task.
- Requests to “just run it” without explaining what the code actually does
How freelancers can protect themselves
1. Verify identities
Cross-check every recruiter and project offer via LinkedIn, the company websites, or official job boards. Avoid responding to tasks that arrive through random social media accounts or direct DMs.
2. Isolate unknown files
Only open suspicious assignments inside a sandbox or virtual machine to prevent infection of your main system.
3. Use scanning tools
Before running anything, upload files to online malware analysis services to check for hidden risks.
How in-house developers can stay safe
- Do not execute external code on company laptops or servers unless cleared by security.
- Forward unexpected assignments or recruiter outreach to your security team.
- Set company rules that block the use of PowerShell, JavaScript, and other scripting tools unless they’re explicitly approved. Where possible, rely on whitelisting to control what can run
- Keep an eye on outbound connections. Attackers often use obscure file-sharing or webhook services to secretly move stolen data.
- Make sure advanced endpoint detection and response (EDR) systems are active. They can catch unusual behavior, such as new scheduled tasks or unauthorized browser activity.
- Protect your saved credentials by turning on MFA for all accounts. Use a password manager instead of storing logins in your browser.
Final thoughts
Cybercriminals know how to exploit seasonal blind spots, and fake coding assignments are just the latest reminder of the creativity these schemes can exhibit. For developers, whether freelance or in-house, the safest approach is to treat every unsolicited task with skepticism and verify it before running anything. With vigilance, layered defenses, and clear security policies, what appears to be a harmless test won’t turn into a costly breach.